Application security to protect customer’s data
Yva.ai solutions architecture
Depending on software settings Yva.ai platform may analyze the digital interactions of employees (passive analytics) and/or may send weekly micro-surveys to the employees (active feedback).
Yva.ai platform supports both on-premise/self-hosted deployment and Yva.ai public cloud services. The following description is valid for both SaaS and on-premise solutions.
Architectural design
Yva.ai uses the following architecture.

For the corporate sources connection, Yva.ai uses the following scheme.
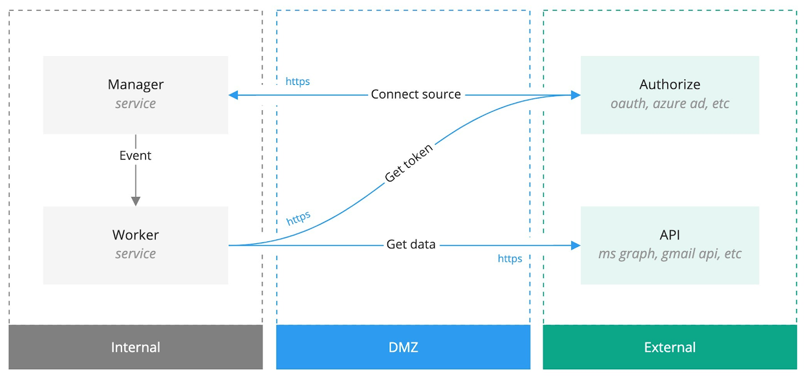
User interaction with Yva.ai
Yva.ai users have access to the necessary information only: for most users, interaction with Yva.ai is limited to responding to surveys and viewing dashboards. By default, Yva.ai anonymizes employee interactions and feedback by aggregating data for groups of at least 5 employees.
A user interacts with Yva.ai through the web interface. Access to the web interface is restricted to authorized users. Yva.ai supports SAML2 and Passwordless authentication protocols. For the Single Sign-on, we use Google OAuth2, Microsoft OAuth2 credentials and SAML 2.0 protocol. The information is provided in the table below.
Used credentials | Scopes |
Google OAuth2 | userinfo.profile, userinfo.email |
Microsoft OAuth2 | User.Read |
SAML 2.0 protocol | email, firstName, lastName |
For the log-in confirmation, Yva.ai sends the client’s employee an email with a one-time code.
The users that are marked as surveys recipients get invitations with the links to 60-second surveys to their emails.
Depending on their role, users can access different dashboards.
Levels of access
Yva.ai supports role-based access control. There are three groups of users: user, manager, administrator, each group has the different privilege to access dashboards and configuration panels.
| User | Manager | Administrator |
My report dashboard | yes | yes | yes |
Company report dashboard |
| yes | yes |
Group Report dashboard |
| yes | yes |
Engagement Quadrant dashboard |
| yes | yes |
Employee report dashboard |
| yes | yes |
Configure the sources, manage Yva.ai users |
|
| yes |
Access and download anonymized data |
|
| yes |
Updates
To ensure optimal performance and security, Yva.ai, Inc. regularly releases patches, fixes, updates and/or enhancements for Yva.ai. The update process can be initiated from the administrator panel and the latest version will be downloaded from our servers. If Yva.ai is installed in an isolated environment, the system can be updated manually by our support engineers.
Support
Technical support via email (support@yva.ai) is available during business hours
Remote assistance is available in case a client provides Yva.ai engineers with remote access to their servers
Yva.ai self-hosted solutions deployment
Yva.ai on-premise/self-hosted deployment means it works within the client's environment and runs on the client's hardware. This way Yva.ai can be used without access to the Internet.
Transmission of information
User data does not transit through Yva.ai, Inc.’s servers; all the data is processed within the client’s infrastructure. The client remains the only operator processing employee data.
Yva.ai, Inc. support team may request logs (Diagnostic Data) that the client may retrieve through the special interface and send to us. Logs may contain some user data, such as email addresses.
The client may grant us the right to use anonymized user data to improve our solutions or to provide additional services outside the scope of the standard deployment. If the client chooses to provide us with the data, it is transferred and stored in encrypted form. The final decision on whether to grant this right lies with the client.
Deployment scheme
Yva.ai is installed and runs on the server on the premises of the client and is connected to data sources, such as mail server MS Exchange, Office 365, G Suite, Slack, and others.
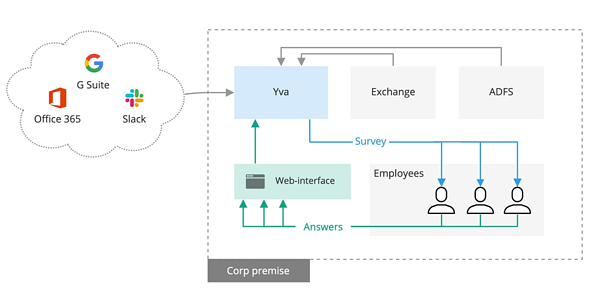
Configuration
The administrator manages Yva.ai users, roles, and their permissions. User lists can be uploaded from AD, G Suite, Office365 or manually. The client can whitelist or blacklist users.
The administrator grants Yva.ai rights to process user data by selecting the data sources they want to connect for each user from the list. For Office 365, G Suite and Slack access are delegated through OAUTH2.
To connect MS Exchange, the mail server requires a service account with permission to access users’ mailboxes. Access to this service account can be limited with the standard tools of MS Exchange.
Encryption of data
Yva.ai processes user data in such a way that as a result, only a part of the metadata that is necessary for the platform to work is saved. In doing so, the textual content is processed using a vectorized representation transformation (patent pending) which does not allow the original content to be obtained after processing.
For the SaaS solution, Yva.ai logically segments the data from each tenant so that it can only be used by this tenant. For the On-premises solution, the data is stored on the tenant's server thus keeping it inside the organization with exclusive access to it.
Text and images vectorization
According to the algorithm shown in the diagram below, the system gets access to the original document in text form. The Encoder is used to convert text to vector form.
Based on the content of the vector, the hashing function is used to get the starting number for initiating a pseudo-random sequence.
For each component of the vector, the following actions are performed: in the context of the initiated sequence, a number from the normal distribution is sampled with a centre at zero and a variation equal to the calibrated value of A.
The new component becomes the sum of the original value and the resulting numeric value.
The obtained vector is the desired form of text representation.
The original text is deleted without the possibility of restoration.
.png?width=544&name=pasted%20image%200%20(12).png)
Secure development lifecycle
Yva.ai is developed using the agile (Kanban) methodology. Continuous, on-the-job training, including secure coding techniques, and coaching are provided to all developers.
Before any public release, extensive regression testing is performed to ensure that the software continues to adhere to design specifications. Our process for reviewing, testing, and deploying code includes peer code reviews, automated and manual testing, and repeatable build and release process. All the software is tested for security.
The testing environment for Yva.ai makes use of test fixtures that reproduce real data patterns. Tests are run in our local development network. Both the testing and development environments are isolated from the live production environment. We do not use user data in our local development and testing environments.
Developers at Yva.ai are familiar with the OWASP Top 10 vulnerabilities and know how to write secure code based on internal documents on secure development and publicly available from OWASP.
Internal document "Secure development policy" is designed specifically for our team. This regulation is intended to define and establish the procedure for managing information security requirements when performing software development at Yva.ai.
During the development process, we use SonarCloud to automatically scan the code. SonarCloud is a cloud-based code analysis service designed to detect problems with code quality in 25 different programming languages, constantly ensuring the maintainability, reliability and security of the code.
Before publishing a product with new functionality, in addition to SAST, we use a DAST scanner to identify potential vulnerabilities missed by the SAST scanner and developers when reviewing the code.
Penetration tests
Yva.ai is performing penetration tests to evaluate the security of the system.
The results of our last penetration test are available per request.
Web application firewall usage
Yva.ai uses the Azure Web Application Firewall for the SaaS solution.